Address CISA Emergency Directive 22-03 Overnight
How Our Cutting-Edge New Capability Makes You More Secure and Compliant With CISA Emergency Directive 22–03.
CISA Emergency Directive 22-03 — Mitigate VMware Vulnerabilities
- This directive was released to highlight in the wild attacks on VMware products.
- Because these products contain remotely exploitable vulnerabilities (ie. CVE-2022-22954 and CVE-2022-22972) that can give attackers full control of VMware systems, agencies are required to either update VMware products or remove them from the network until they can do so.
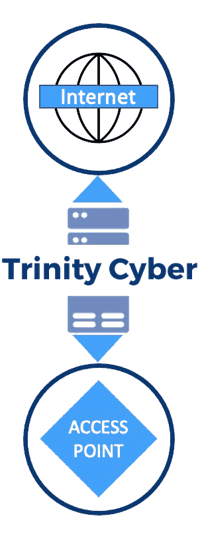
- Trinity Cyber protects Internet facing VMware servers from initial attack, using unique technology - run as a fully managed service - to stop exploits inline, before they have a chance to compromise VMware platforms.
- Agencies can patch these systems while ensuring that Remote Code Exploits (RCEs) such as the ones called out in this directive, never reach mission-critical devices.
Learn More About Each Mandate
CISA ED 22-03 Compliance
Trinity Cyber automatically protects against the exploitation of hundreds of vulnerabilities, including the VMware vulnerabilities for which CISA has directed mitigation
Example
CVE-2022-22954, an RCE in VMware Workspace ONE Access via server-side template injection (SSTI), allows attackers to fully take over a vulnerable system with crafted web request. Trinity Cyber detects the exploit content in these web requests and completely removes it without ending the web session. The VMware server responds back to a blank web request, confusing attackers. With Trinity Cyber, attackers don't know that their exploit failed and security teams get rich telemetry about what was prevented, allowing them to understand exactly what the attacker tried to do.
Example
CVE-2022-22972 is another RCE in VMware Workspace ONE Access. Attackers exploit this vulnerability to bypass normal authentication and gain administrative access without having to "log in". As a result, they can gain full control over VMware devices by sending a web request that tricks a login server to provide admin credentials to a waiting attacker. From there, attackers use these credentials to log in and perform further attacks. Trinity Cyber detects authentications bypasses and completely prevents them from going to a valid login server. Attackers never get valid credentials back, meanwhile security teams can see every exploit attempt they try - giving ultimate visibility.