Address M-19-26 Overnight
How Our Cutting-Edge New Capability Makes You More Secure and Compliant With M-19-26
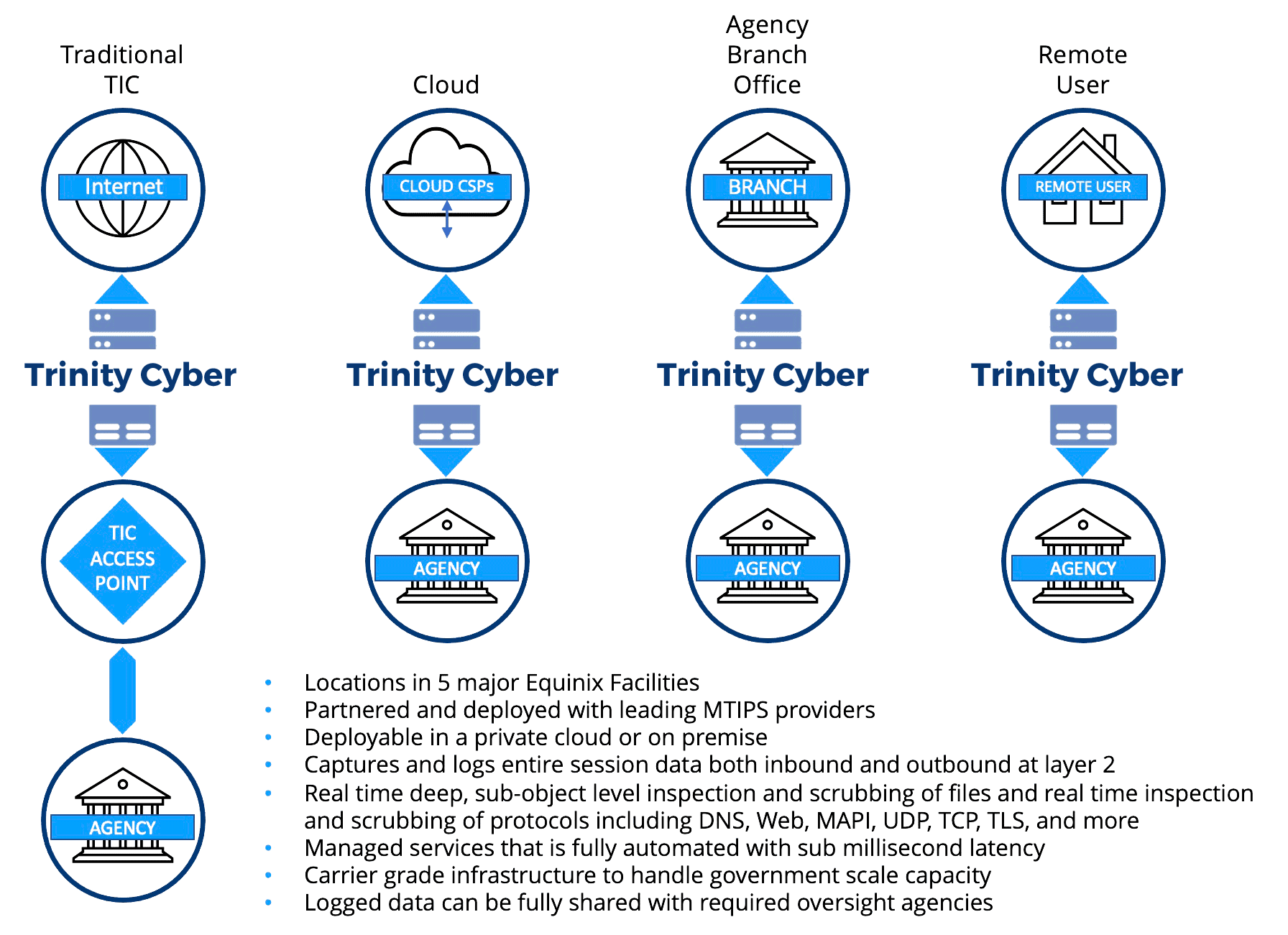
M-19-26 — Update to the Trusted Internet Connections (TIC) Initiative
- One of the tenants of this memo requires agencies to perform full packet capture and leverage SaaS solutions. Trinity Cyber and our partners can provide both functions.
- As a carrier grade threat mitigation and prevention solution, Trinity Cyber has been architected to sit at the TIC Internet Access Points (IAPs) of your organization to offer full inspection and protection of your inbound and outbound data.
- Because Trinity Cyber's solution sits inline and performs actions automatically with sub-second latency, it facilitates the delivery of mission capabilities.
Learn More About Each Mandate
M-19-26 Use Cases