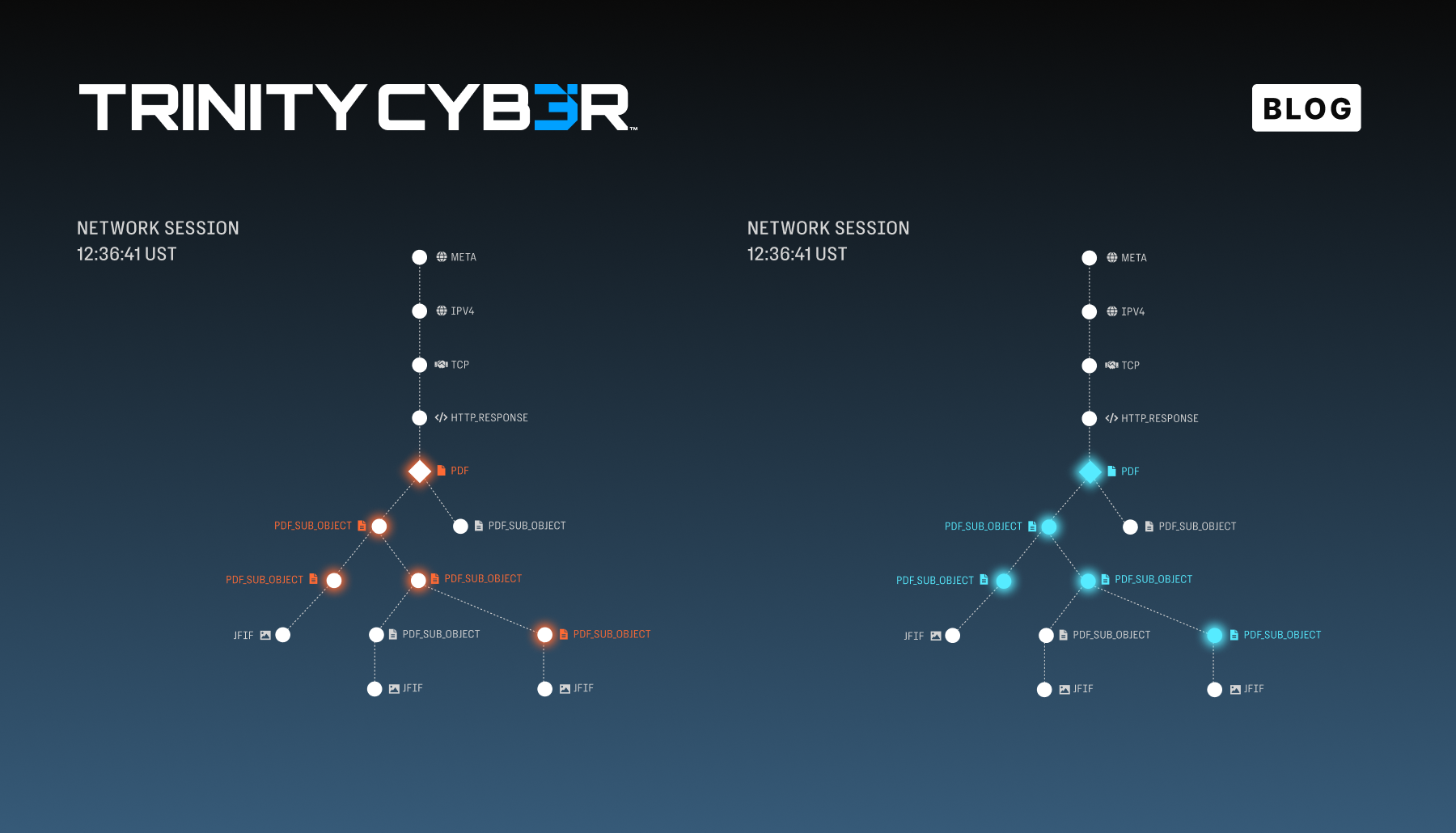
Typically, cybersecurity teams are playing defense, often only responding to critical threats after they have become incidents and breaches. The exhausting detect-and-respond cycle favors the adversary, keeping defenders in a constant reactive state.
Today, there is a better way forward. Trinity Cyber helps customers achieve their business outcomes with threat defense built for what’s now, and what’s next. Our patented Full Content Inspection (FCI) technology is the first practical, active cyber defense solution eliminating threats in real time — before your data and operations are at risk.
Explore below how Full Content Inspection can be your key to rationalizing and transforming your cybersecurity strategy.
1. A proven solution protecting over 3 million users globally
Mission-driven and innovation-focused, we were first available to U.S. government customers. Now, we are the choice for leading banks, credit unions, manufacturers, utilities, and more demanding serious security coupled with lower total cost.
Customers have measurably better outcomes with Trinity Cyber:
- FCI operates transparently. Users don’t notice it, accelerating adoption.
- We protect IT and security teams from both 1) threats, and 2) the failed “detect-and-respond” approach that is too slow and too costly for most organizations.
- Even companies with fewer than 100 employees find Trinity Cyber cost-effective, as our unique approach does not depend upon active administration.
2. Assure business continuity with real-time threat removal
Business operations depend upon both network uptime and full operational uptime. Uptime must be assured in the face of cyber threats. Trinity Cyber Full Content Inspection (FCI) redefines what customers should expect in threat defense as FCI does not simply detect threats — it actively removes them from live network traffic with sub-millisecond latency, so your users do not notice a difference.
FCI delivers surgical precision, fully opening, inspecting, and removing malicious payloads and unauthorized data from content, all without slowing down users, interrupting sessions, or impeding your operations. Our proprietary AI models (noted further below) accelerate highly accurate file type detection.
Trinity Cyber’s threat detection approach focuses on identifying the adversary techniques, tactics, and procedures (TTPs). By focusing on TTPs, we protect customers by catching entire classes of threats — even as they evolve. Our Threat Analysis team builds detections for FCI. It is one of the world’s most focused research groups regarding TTP-based detection development.
If you take a free trial of our service, you will see for yourself that FCI stops threats that legacy IPS, SWG, and NGFW miss. And as our capability is delivered as a cloud-delivered service with automatic inline response, we are redefining what Managed Detection and Response (MDR) should look like for a significant share of the market. Our global platform analyzes over 2 trillion content objects daily, and mitigates millions of threats each month, all with less than one millisecond of added latency in our parsing and threat detection.
Status quo incident response strategies assume your security will fail. While there are no silver bullets in security, wouldn’t you rather have, as your first line of defense, a trusted and proven prevention solution? Even if you have the budget for a full Incident Response program, wouldn’t you rather have an elite team of operators hunting on your behalf, instead of your being stuck in reactive posture?
Learn more about FCI's performance and precision.
3. Select security built for the real world
Traditional security tools rely on indicators of compromise (IOCs), like malicious URLs and hashes, to identify threats. This incomplete strategy is easy for hackers to evade and has kept organizations struggling for practical ransomware and phishing defense. FCI changes the game by proactively targeting attacker tools, techniques, tactics, and procedures (TTPs) with impressive results.
Further, false positives plummet, so you can depend on your security to not interfere with your operations. Strong detection is, in practice, meaningless if it’s accompanied by false positives that keep you from using it. FCI’s false positive rate is less than 0.01%. Compared to even a well-tuned legacy IPS, this represents a 500-fold improvement. Trinity Cyber means less noise and greater confidence that threats are automatically neutralized. When you do a proof-of-value exercise with us, you’ll discover that you can use us without concern that you are breaking user and machine workflows.
Review real-world FCI use cases.
4. Stop chasing alerts with our AI-accelerated prevention
Detection isn’t the same as prevention. The unending cycle of threat detection and incident response is an exhausting game of catch-up where the attacker has an advantage.
Instead of chasing alerts, we enable your IT and security teams to be more efficient and productive. FCI proactively protects, simply providing you with notification when threats are removed. The Trinity Cyber customer portal provides full detail and transparency into where threats appeared and were removed from live traffic.
Part of how we’re able to operate in real-time is with proprietary AI models that we’ve developed that protect your revenue, operations, and business continuity. Our models are securely developed with millions of files of training data in an air-gapped environment. Then, the models are employed with our unmatched visibility from discovering threats in the 2 trillion content objects we inspect daily. The result? Enhanced threat protection. And unlike other leading AI models for file identification that identify content at 5-86 milliseconds per file, Trinity Cyber's models execute on average in .22 milliseconds (220 microseconds). The result? Enhanced real-time threat protection.
5. Security without stress: FCI is delivered as an automated managed service
Security teams using outdated network security solutions that only notify you after an attack occurs are overwhelmed with alerts and dashboards. With FCI, Trinity Cyber handles the heavy lifting. Our centrally managed threat prevention platform is fully automated for hands-off security.- No alert fatigue. Trinity Cyber triages each threat and sends a simple notification letting you know the issue is handled.
- Complete Network Insight. Review 72 hours of decrypted, searchable PCAP data with easy portal access and scalable storage.
- No extra effort required. Your team stays informed and your network remains protected without adding to your workload.
Explore our centrally managed platform.
Start Preventing Attacks with FCI
The cybersecurity industry has over-rotated towards incident response, at the expense of threat defense innovation. With FCI, the dynamics change: you’re no longer stuck responding to threats after the fact. FCI examines all content before it enters or exits your network and disrupts more adversary actions before they can succeed.
FCI is not about simply detecting threats. It actually eliminates them inline, in real time.
Schedule a live demo
to see how Full Content Inspection by Trinity Cyber can help your organization flip the script on traditional cybersecurity.