The Edge. Evolved.
Meet the most profound technological breakthrough in network security technology in the last 20 years.
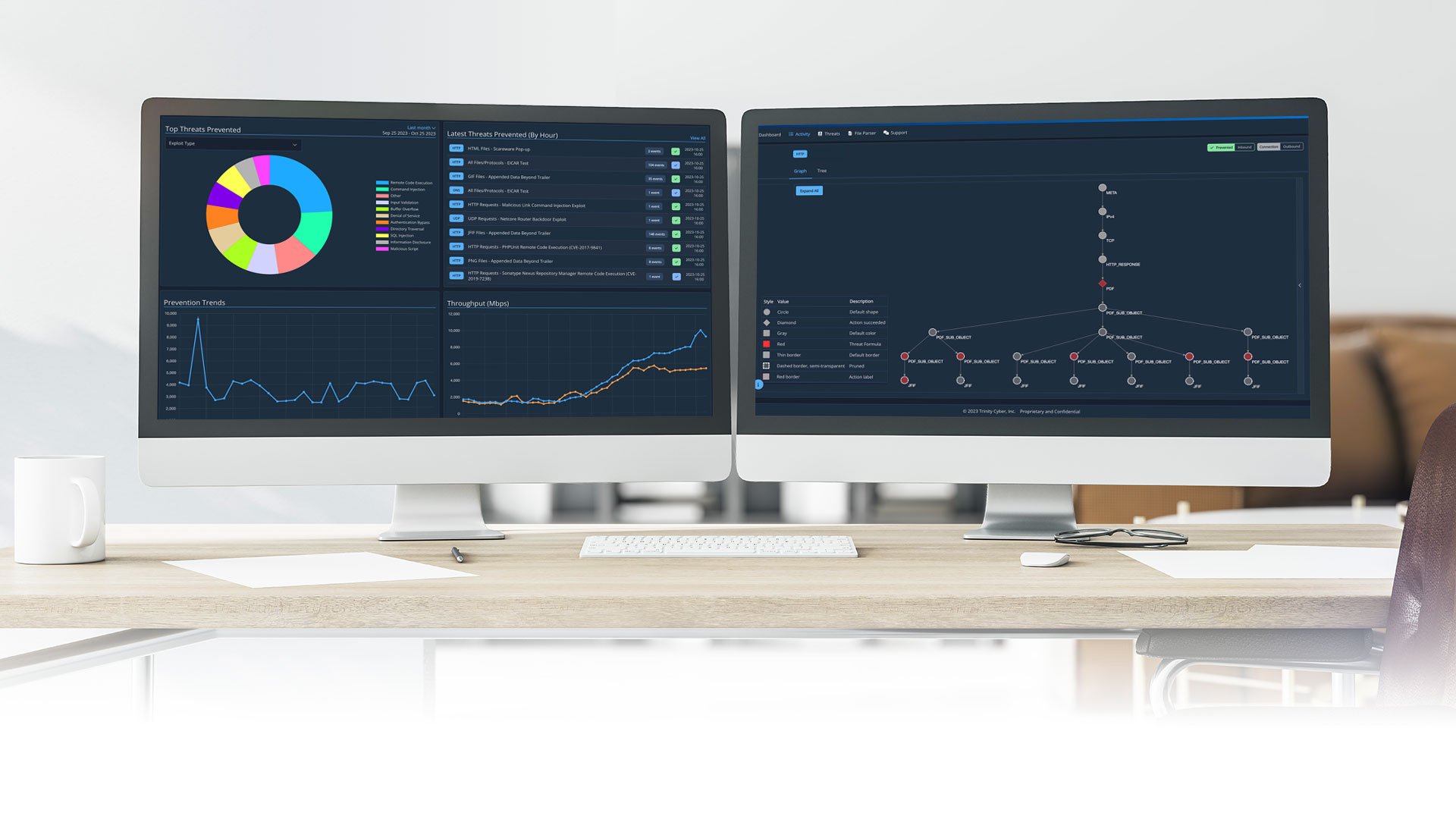
A Fully Managed Threat Prevention Capability with Groundbreaking Insight and Context
Forget Seats. Forget Licenses. Discover Pure Value.
From Our Clients
"Trinity Cyber has completely changed the way we protect our customers, and how we run our business. False positives are a rare occurrence, which has definitely had a positive impact on my team’s morale and burnout rate."
-- Wayne Porter
Allegany Computer Services
Be Compliant Tomorrow.
Compliance does not equal security, but it’s a reality we all face. Subscribing to Trinity Cyber puts a new capability in the path of your Internet traffic and allows you to comply with dozens of requirements and directives—and it actually improves your security.
It’s Not Outsourcing, It’s Way More Than That.

Awards & Recognition








